Once in awhile a service may get compromised script or item in it – in a recent case, a Zoom link will actually take you to some random site as part of some sort of adware campaign??? However a closer look shows it is very important to test your links on email or sites:
The link I saw recently actually had a very odd looking script – script in a production service is generally minified sometimes, but won’t be oddly obfuscated or base64-encoded. The suspicious part of this script starts out in the <body> with an odd looking launchBase64:
<meta property="og:title" content="Join our Cloud HD Video Meeting">
<meta property="og:description" content="Zoom is the leader in modern enterprise video communications, with an easy, reliable cloud platform for video and audio conferencing, chat, and webinars across mobile, desktop, and room systems. Zoom Rooms is the original software-based conference room solution used around the world in board, conference, huddle, and training rooms, as well as executive offices and classrooms. Founded in 2011, Zoom helps businesses and organizations bring their teams together in a frictionless environment to get more done. Zoom is a publicly traded company headquartered in San Jose, CA.">
<meta property="og:url" content="https://us02web.zoom.us/j/81618471557">
<meta property="og:site_name" content="Zoom Video">
<meta property="fb:app_id" content="113289095462482">
<meta property="twitter:account_id" content="522701657">
<script nonce="stRXxqc7T3GWI-t5MI1yMw" src="/lres"></script>
<link rel="shortcut icon" href="/zoom.ico">
</head>
<body>
<script nonce="stRXxqc7T3GWI-t5MI1yMw">
window.launchBase64 = "Go8CCkwIARAAGAEgACogaG1iamJqZHBrb2JkanBsZm9iaGxqbmRmZGZkaXBqaGcyIGZjcG9jZ2xhYm9naGZraWhqYmFpbmRmYWZwZmliY2hvEr4BCAASCC56b29tLnVzGAAgACgBMAA44KcSQhkrMTY2OTkwMDY4MzMsODE2MTg0NzE1NTcjQhkrMTM0NjI0ODc3OTksODE2MTg0NzE1NTcjQhkrMTI1MzIxNTg3ODIsODE2MTg0NzE1NTcjQhkrMTMxMjYyNjY3OTksODE2MTg0NzE1NTcjQhkrMTkyOTIwNTYwOTksODE2MTg0NzE1NTcjQhkrMTMwMTcxNTg1OTIsODE2MTg0NzE1NTcjSgJVUyLCCQocaHR0cHM6Ly91czAyd2ViLnpvb20udXMvd2ptZhINL3Bvc3RhdHRlbmRlZRoraHR0cHM6Ly91czAyd2ViLnpvb20udXMvd2Mvam9pbi84MTYxODQ3MTU1NyLZA2h0dHBzOi8vdXMwMndlYi56b29tLnVzL2xhdW5jaC9kb3dubG9hZC90ZDdTY0hwVnBucDQzbVdSRXNMa19MV2dhQ3FUam9oWUtrUGZSZ29JLVY5MzdfbDdZNVNSaURIdVNEUGVTNjROR1BPcmhMdUFlbHplU0xwZnJUVy1mNWpFX0FPc3Z0QzVaWUlmUGtWdm5tTXZaWWl4UXNmR2JfTGJWeHJlZ05pRURsY1lJdmhjUzVmUW1ldXB1VWNpbGJ6NzJvUE1qRWRtLUNlWkw5TDVTYTkxa3diSlZCZ1pOVHRvYW5SS1BMWHNKdWZVOUl6VlhpTUJzTDBhTjdMSWdEZGd6eWRSUUY2b0hMWDBrOWFRZXBFcEsxREhkdkFoRzg2R3FsZ3VpTTF5V1RUMERTbVktd2R4N2Nwb3lwNU1uYmRPQmNMMGpaUGk1RkRqV1FtRTlhb0stUjkxRzQtNEp2c1ZqUE54bk5LaWRXNUtoYVFlVk5xTGZzZDN0RXlyOHBHVlA3U0ItSnZIZlEuM0V2d0g4YjFxQ1lQbGp5Ny9tZWV0aW5nL2hRdVdrZHJIbTA1b3BGRXFZNEFIWFNGTEg2SmJXVFZvdmxONS5kQW5id3pvM1ZfUS1xcHpNKhFab29tX2xhdW5jaGVyLmV4ZTovaXRtcy1hcHBzOi8vaXR1bmVzLmFwcGxlLmNvbS91cy9hcHAvaWQ1NDY1MDUzMDdCIGh0dHBzOi8vdXMwMndlYi56b29tLnVzL2Rvd25sb2FkSjdodHRwczovL3VzMDJ3ZWIuem9vbS51cy9jbGllbnQvbGF0ZXN0L1pvb21JbnN0YWxsZXIuZXhlUkFodHRwczovL3VzMDJ3ZWIuem9vbS51cy9jbGllbnQvNS4wLjI2MjEzLjA2MDIvWm9vbUluc3RhbGxlclhQLmV4ZVouaHR0cHM6Ly91czAyd2ViLnpvb20udXMvY2xpZW50L2xhdGVzdC9ab29tLnBrZ2JBaHR0cHM6Ly91czAyd2ViLnpvb20udXMvY2xpZW50LzMuNi4xMDgyNi4xMTAxL3pvb211c0luc3RhbGxlci5wa2dqQWh0dHBzOi8vdXMwMndlYi56b29tLnVzL2NsaWVudC80LjEuMzUzNzQuMTIxNy96b29tdXNJbnN0YWxsZXIucGtnckFodHRwczovL3VzMDJ3ZWIuem9vbS51cy9jbGllbnQvNC4xLjM1Mzc0LjEyMTcvem9vbXVzSW5zdGFsbGVyLnBrZ3pDaHR0cHM6Ly9wbGF5Lmdvb2dsZS5jb20vc3RvcmUvYXBwcy9kZXRhaWxzP2lkPXVzLnpvb20udmlkZW9tZWV0aW5nc4IBLmh0dHBzOi8vdXMwMndlYi56b29tLnVzL2NsaWVudC9sYXRlc3Qvem9vbS5hcGuKAThodHRwczovL3VzMDJ3ZWIuem9vbS51cy9jbGllbnQvNC41LjU2OTkuMTAyNy96b29tNS4wLmFwayr5AQixvtOV8i4aD3VzMDJ3ZWIuem9vbS51cyIEam9pbirYAQoYZVZ1MDdDQnBSUGF1ZGVlMTVtSlRjZz09EIWV3IawAjIAagRqb2lucAB6DzAuOTIuMTEyMjcuMDkyOYIBAIoBc3lxQ3J4QTJ2VFMzbXlmb1ZJNmxKNnMzeGExMVl6UFlVeUdDQVdUWm9KY05wYVFnUFJDdXlTRXdXdV9tVDRGSWx0U1VaWkdoMXJVQmt4ZnBtVDlYYjlJaGpSM1RDVUtDX1BnLlJOWF91Uk5SOVk1UjhzT0KSASBjZDViZTkwNzk5MmQ0NDE5OTM5Yzc2ODc3MjFjZjQ2OA==";
(function () {
var js = (JSON.parse("{\"js\":[\"launch-meeting/meeting....
and continues with what you would expect as a normal zoom script below. The base64’d script seems to have zoom.us download links, but a quick search for this “launchBase64” finds this analysis that shows malicious IP addresses a similar link may be connecting to.
A second look at this link, however, finds that the url itself goes to a completely normal Zoom link. Normal zoom links actually have that base64 item, so… false alarm? Clicking the link brings us to some random ad-ware on the internet… Wix or Nordvpn or some random addon that it wants you to install to continue… etc.
A closer look finds that the right click copy link, will give a link like:
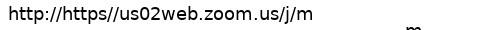
Note the lack of https:// which is the valid scheme of the url. You’ll note the browser takes you to https dot com which redirects to a random affiliate link or ad page on the internet.
Why? and how we can prevent it
This appears to be some sort of link harvesting bug, which takes advantage of mistyped urls and likely makes someone a lot of money on ad click revenue or distribution of distributed spyware such as pages are used by users expecting the valid link from a valid source… but where did it come from? It most likely was added in a system that adds http:// to any url that doesn’t have the url. That would be a good idea if you just enter a domain like “bing.com” or “google.com” but in this case where the full url was typed but without a : the browser tries its best to find the url, going to this random ad-generating domain.
What can you do?
- When you make a link, test it and do not add http:// twice… or misspelled.
- Report these affiliate links or malware as you see them. Firefox Help -> Report Deceptive Site is a good feature.
- Add to /etc/hosts a block for this domain:
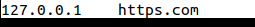
and that should block going to this domain… but in Firefox this may not work due to its DNS over https feature.